
Pave the way for distributed clouds on premises
People LOVE change, IF coming in the right proportion, at the right time and in the right way. Why don't we start small and produce guides for others to join ...
Published on Nov 07, 2024

Exploding hand-helds
Exploding hand-held devices such as pagers, radios and walkie-talkies to maim people was a targeted attack. It can not happen to us. It happened there, in Beirut, far from our beds.
Published on Sept 25, 2024

Upgrading to Noble Numbat
The software updater tool prompted about the available upgrade to Noble Numbat. For a change, I decided to try the do-release-upgrade script. Ugh. Hold off, or shoot troubles.
Published on Sept 13, 2024
The European Union must keep funding free software
Open Letter to the European Commission, initially published by petites singularités, English translation provided by OW2.
Published on July 22, 2024
Time to choose a new password?
Ever longer, complex passwords (knowledge), augmented by MFA (possession), with all passwords encrypted in transit and at rest, further enhanced by biometrics (what we are). And we're all using it, aren't we?
Published on February 24, 2023
Capturing credentials
The most common technical attack method is hacking credentials and authentication mechanisms. Techniques adversaries use to capture credentials include finding or guessing credentials, and passing or relaying password hashes.
Published on February 24, 2023

Defendable internet?
A redesign of the Internet to make it an open, transparent, and yet secure internet for all to enjoy is possible.
Then why we are not building such a defendable internet?
Published on February 2, 2023

And now for something completely different
And when you least expect it, there is a Larch. Authorities in Europe are responding to GDPR violations ... most importantly, the Transparency & Consent Framework (TCF)
Published on February 15, 2022

No wai
The UN Shared Rohingya Data Without Informed Consent putting the lives of people at risk. The UN comments on that with a Statement and what follows is an explosion of articles and statements on the internet.
Published on June 24, 2021

Grey areas
The creation of legal grey areas, per three examples, using the example of sexual consent for clarity and because that is where the consent concept originated and is expanding from every day life for digital consent.
Published on May 07, 2021
Internet (in)security trends
Gotta feel kind of bad for nation-state hackers who spend years implanting and cultivating some hardware exploit, only to discover the entire target database is already exposed to anyone with a web browser.
Published on April 22, 2021
Panopticon
Social theorist Jeremy Bentham's original projection for a panoptic prison, made it so a prisoner never knew if he was being watched. A circular prison with a single guard tower in the middle was the original blueprint for the structure.
Published on April 22, 2021

It is not enough!
The GDPR and ICCPR are not enough, and that is not only because of the tremendous struggle to implement their rules. The GDPR for example, actually legitimises the entire information industry by making it a grey area.
Published on April 21, 2021
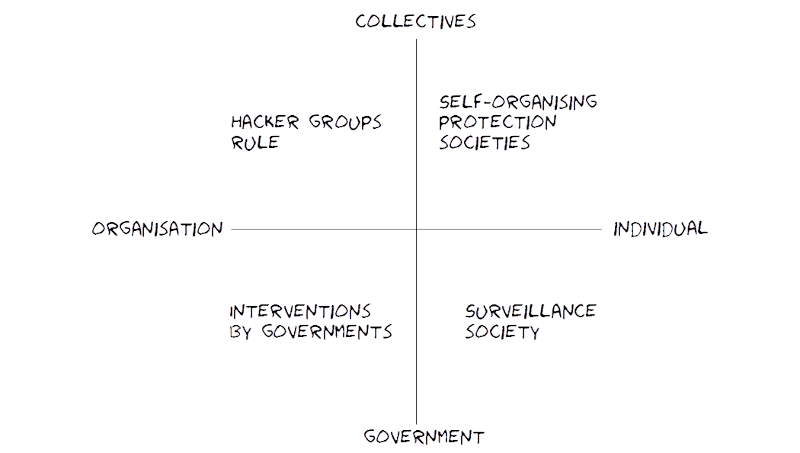
Scenario logics
Scenario logic: Plots, likely effects, measurables and observables for five scenarios: Surveillance society, Interventions by governments, Hacker groups rule, Self-organising (protection) societies, and Obliviousness and congruence.
Published on April 06, 2021
Legitimisation patterns
Legitimate power is based on a structural relationship (economic stratification or other forms of hierarchy) between influencing agents and targets. Implicitly, or explicitly, the agent says, “I have a right to ask you to do this, and you have an obligation to comply”.
Published on October 13, 2020

Governmental ghost stories
This old-fashioned horror anthology isn't terrifying or scream-inducing; instead, it is closer in spirit to the moody, clammy, atmospheric English movies of decades past, and parodies thereof. A ghostly proposal from GCHQ. We are reminded of Dr. Strangelove.
Published on February 17, 2020

Surveillance architecture
Chances are that every document you create, every digital photograph you take, every music file you download, and so on, all have little bits of metadata which can leak vital information about your identity, and surveillance and censorship go hand in hand ...
Published on November 02, 2019

Information war technology
States are attacking other states, their own people for maintaining dominance, corporations do to get you to buy their stuff, political groups are attacking other political groups for believing in something else, and individuals take out their frustration on others.
Published on September 27, 2019

Universal Declaration of Human Rights (UDHR)
The UDHR consists of 30 articles affirming an individual's rights which, although not legally binding in themselves, have been elaborated in international treaties, economic transfers, regional human rights instruments, national constitutions, and other laws.
Published on September 08, 2019
Corporate surveillance state
There was of course no way of knowing whether you were being watched at any given moment. How often, or on what system, the Thought Police plugged in on any individual wire was guesswork. It was even conceivable that they watched everybody all the time.
Published on May 17, 2019
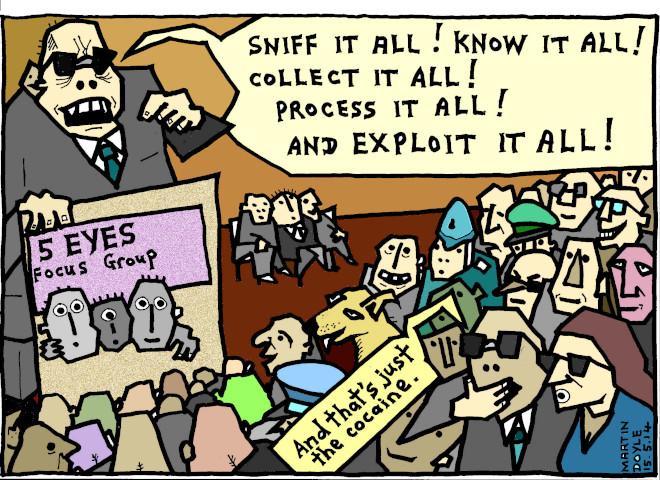
Five Eyes alliance
The UKUSA agreement was signed in March 1946 for cooperation in signals intelligence between the UK and the USA. It included more and more countries, and was a secret agreement until the Australian Defence Signals Directorate disclosed it.
Updated on August 28, 2018

International Covenant on Civil and Political Rights (ICCPR)
No one shall be subjected to arbitrary or unlawful interference with his privacy, family, home or correspondence, nor to unlawful attacks on his honour and reputation.
Published on May 15, 2018

OECD Recommendations
The OECD provides a platform to identify good practices and coordinate domestic and international policies of its members. The United States, while endorsing the recommendations, is not implementing them.
Published on May 15, 2018

Data retention legislation EU
The basic standard laid down by the CJEU is not even adhered to by most EU member states, despite their legal obligation to comply with the Court’s jurisprudence.
Published on April 15, 2018

General Data Protection Regulation (GDPR)
The old Data Protection Directive of 1995 was outdated. It failed to cover social networking sites, cloud computing, location-based services, smart cards and biometric data.
Published on April 15, 2018