Time to choose a new password?
by Ty Myrddin
Published on February 24, 2023
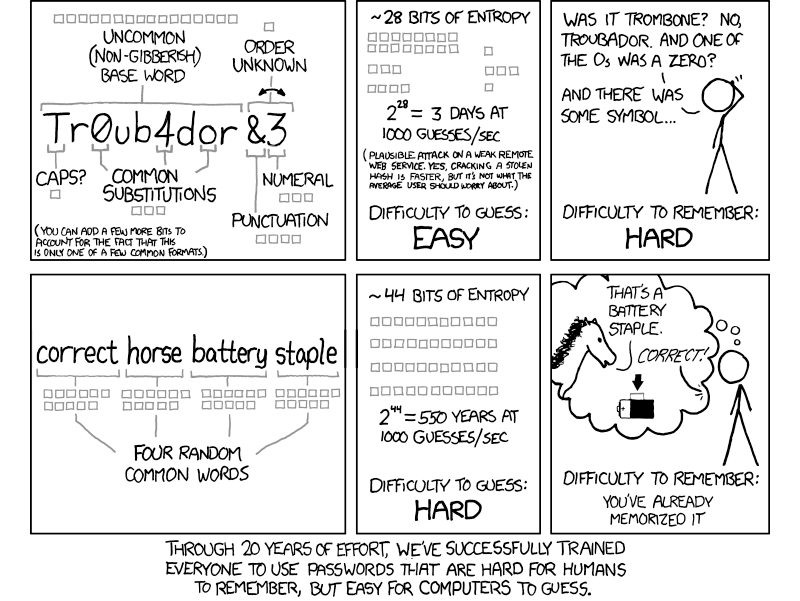
Currently perceived state
Maintaining security demands ever longer, complex passwords with frequent changes, now augmented by installing and using multifactor authentication (MFA), with all passwords encrypted in transit and either encrypted or hashed at rest, and further augmented with biometrics. And we're all using it to protect our PII.
Really?
- In 2019, Microsoft found 44 million of its users had used the same password on more than one account. According to a 2019 Google study, almost two-thirds of people use the same password across multiple accounts. And apparently, IT professionals reuse passwords more than average users. They have, of course, more accounts to log into than the average user.
- The most popular passwords are extremely easy to guess. A lot of people use their name or birthdate in their password.
- The 2019 HYPR study revealed that lots of people rely on memory to manage their work passwords.
- Also, in 2020, according to The Ponemon State of Password and Authentication Security Behaviors Report, a little less than half of organisations still rely on sticky notes for password management.
- And share their password with someone else, even their email account password.
- In the HYPR 2022 report, 80% of reported breaches are due to authentication weaknesses, yet 90% believe their authentication approach is secure, and 63% kept their insecure authentication methods after a breach.
- More than half of users would prefer an alternative method to passwords.
People are frustrated with passwords and just wish for the simplest access possible, instead of having to carry a cognitive burden, and having to jump through hoops all the time to keep their PII safe and secure.
Future developments
All passwords and passphrases will be obsolete.
This is not unlikely to happen: The increase in affordable computing power provided by the cloud is not only providing companies application resources, but also providing adversaries with more password-cracking resources. Meanwhile, users continue to choose weak passwords, and as a result, there is a strong push to support alternative identification and authentication mechanisms.
Mechanisms going beyond something one knows (password) and/or something one possesses (phone, fob) and/or even what one is (fingerprint, retinal print). Maybe we'll be using who one is, in the form of episodic memory because who are we but the stories we tell (ourselves), or in the form of our thoughts, because "I think therefor I am" ...

Raw magic crackled from their spines, earthing itself harmlessly in the copper rails nailed to every shelf for that very purpose. Faint traceries of blue fire crawled across the bookcases and there was a sound, a papery whispering, such as might come from a colony of roosting starlings. In the silence of the night the books talked to one another. A student