Scenario logics
by Ty Myrddin
Published on April 26, 2022,
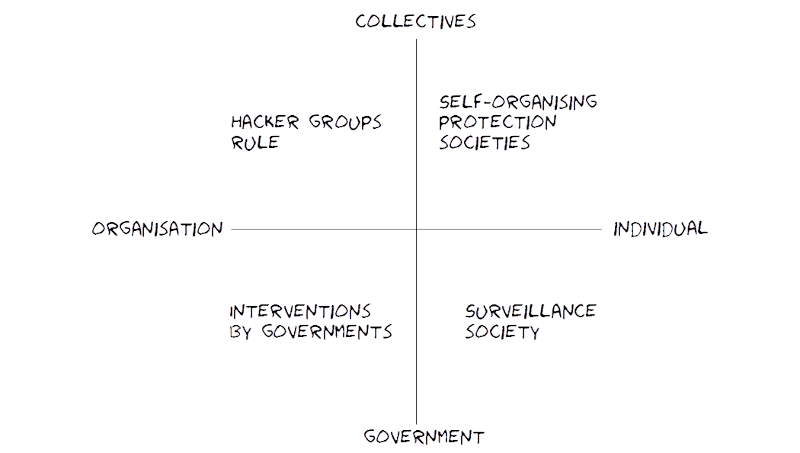
From a scenario planning done in 2013, with some of the measurables and observables that had appeared by 2022:
Obliviousness and congruence
Plot
In scenario planning everything is a prediction. None of it is real. All predictions are wrong. And that which gets overlooked in most (if not all) digital scenarios is reality. For example:
- We belong to a finite planet, with finite resources.
Likely effects
- Constraints on economic development (but not for transnational players in the neoliberal network).
- Corporations and businesses already show a trend of making employees make do with what they have and requests made by employees for better resources (to serve customers with) are ignored, leaving employees in a very difficult place – unable to do their job properly and on top of that, likely to be penalised for ‘poor performance’. This could lead to people feeling burned out and frustrated. Performance will drop as a result and so will demand and profits.
- Instead of dealing with it (just as with addicts facing a scarcity of the resource they are dependent on), over-use of resources, such as the depletion of rain forests and over-fishing can occur.
- Opportunism can increase.
- Misuse of scarce resources is also likely.
- The effect of inflation tends to be stronger for low-income individuals, whom inflation renders relatively more vulnerable, thereby increasing inequality.
- Lack of material resources - chronic (low income) and situational (inflation) lack of material resources - causes people to make harsher moral judgments and be more (often) physically ill.
Measurables and observables
- Many of the metals needed to feed the surging global demand for high-tech products, from smartphones to solar panels, cannot be replaced, according to a Yale study, On the materials basis of modern society
- The British Geological Survey (BGS) Risk List states that economically important metals with high levels of risk to supply disruption including antimony (with application as a fire retardant), bismuth (used in numerous medical applications), platinum group metals (active components in auto-catalysts), and tungsten (a key hard metal used in most cutting tools), particularly the rare earth elements and antimony, have low recycling rates and a limited number of substitutes. They are also almost exclusively mined as by-product metals.
- The minimum total power that was required to run (wall socket power) and maintain (embody) the internet in 2017 was guesstimated to be somewhere between ~131 GW + ~167 GW = ~298 GW and ~204 GW + ~288 GW = ~492 GW.
Surveillance society
Plot
- A government steps in to protect its citizens from (potential) dissident and/or criminal actions and/or information that might “corrupt” its citizens.
- (Intelligence) Agencies use data-mining to identify (potential) individual dissidents and criminals.
- Government steps in to protect its individual citizens’ privacy from being mined by non-state-actors and to create distraction from their own mining activities. Strong privacy regulations emerge.
- Citizens are increasingly being targeted in surveillance with surveillance tools purchased from China.
Likely effects
- Organisations (Cartels, corporations, companies, NGO’s) are restricted in their use of data.
- Consumerism is stifled.
- Governments will try to shift responsibility to individual citizens.
- Identity theft and ransomware boom.
- Individual citizens and citizen groups supported by NGO’s call for “making the internet more safe (for children/women/dissidents)”.
- Governments try to regulate again and surveillance increases.
- Companies offering private and protected access to online services and make a lot of money.
- Mobile devices are closed and curated.
- Because people need to appear perfect to others, the need to appear perfect to oneself increases also (the cognitive dissonance is too painful). Acknowledging mistakes and failures and the feelings associated with them can be hard.
- The surveillance society makes people have “negative
emotions”. The positive thinking movement encourages people to
ignore their negative emotions.
- Negative emotions get buried in subconscious, resulting in mood swings, unexplained sadness, and mild depression, and eventually in aggression.
- Suppressing negative emotions may lead to depression, low self-esteem, and even physical illness in extreme cases.
- Suppressing emotions is a risk factor in premature death, including death from cancer.
- Negative emotions are dumped elsewhere on innocent people. NGO’s will need more funding to respond with new/more support for women and children (at home) and dissidents (elsewhere).
- Consciously constantly suppressing emotions can cause emotional numbness. It is common to hear the phrases “We live in stressful times” and “It is what it is” (with a shrug) and “You shouldn’t feel this way. Everything is alright. You need to be positive.”
Measurables and observables
- The attack patterns may or may not have to do with
psychogenic forces and deep states and include
- women and children more targeted more by teensy weensy petty tyrants, little petty tyrants and minor petty tyrants.
- human rights activists, journalists, land defenders, and political dissidents targeted more by petty tyrants.
- identity theft and ransomware attacks happening via automated botnets.
- (Intelligence) Agencies increasingly using data-mining or bying data from brokers to identify “(potential) individual dissidents and criminals”.
- The old EU Data Protection Directive of 1995 was outdated.
It failed to cover for example, social networking sites, cloud
computing, location-based services, smart cards and biometric
data, and in 2012 the European Commission proposed a
comprehensive reform of the EU’s data protection rules to
strengthen privacy rights and boost Europe’s digital economy.
Unlike directives, the new GDPR that came into force in 2018
does not require national governments to pass any enabling
legislation. It is directly binding and applicable.
- Note that the GDPR only addresses privacy concerns related to data processing by private sector and not by individual Member States. With the internet being a global network (driven by established interests), laws regarding for example, digital fingerprinting by intelligence agencies, may develop completely differently from one country to another regardless of raised concerns at the EU level as to the compatibility of such activities with human rights standards.
Interventions by governments
Plot
- Corporations, enterprises and NGO’s are targets in this scenario.
- A government attempts to regulate the situation in order to protect the targets and itself.
- All infrastructure becomes critical.
- The targets are held responsible.
- Attacks are perceived as cyber war events.
- Cyber warfare breaks out.
Likely effects
- Increased cost (capital) for businesses/organisations online.
- Increasingly business resources are focused on compliance with regulation instead of risk assessments for gaining a profit.
- Botnets get taken down.
- More cyber criminals are caught. Opportunity cost for private petty tyrants increases.
Measurables and observables
- The attack patterns that the (in)famous Equifax (and other) data breaches reveal, is one of negligence - only self, no real concern for customers/clients/citizens and the context of the internet. This invites government regulation while such vulnerable products do not invite perceptions of sophisticated hacking on infrastructure by other nations and acts of cyberwar that call for counterattacks. On the contrary. The JP Morgan Chase hack is a prime example of immediately perceiving cyberwar after a breach is made known. When discovered in 2014, the media were full of articles on Russian hackers attacking the U.S. financial system in retaliation against U.S. government-sponsored sanctions aimed at Russia. As it turns out in 2015, it was a “worldwide hacking ring” with four members, of which one was an American and two were Israeli’s. The fourth remains a mystery. That Aaron, after attacking the U.S. Financial system (read “crown jewels”), fled to Russia just weeks before the U.S. issued arrest warrants for him, and then later negotiated with the U.S. to come back home, seems also significant.
- Forming of cyber defence divisions like the NATO Cyber defence, NATO Cooperative Cyber Defence Centre of Excellence, and Cyber Warfare book by Defense One portal
- Emerging infrastructure studies like Harvard: Cyber War
- Appearance of International Cyberwar Treaties: Calls for such treaties, intiatives, frameworks made, and discussions on pros and cons, but a treaty like this makes no sense and is extremely unlikely to work in practice as governments continue to invest millions in developing espionage technology to spy on each other, and such targets include allies.
Hacker groups rule
Plot
- Autonomous collectives, cartel-paid mercenary and nation-state-sponsored hacker groups grow, expand and escalate.
- Cartels that have the resources to respond with “security measures” also grow, expand, and escalate.
- Some cartels establish “safe havens” (fiefdoms) and will start charging (a lot) for membership or require more private data from its “members” to “cover the costs”.
Likely effects
- Increase in attacks.
- Security costs escalate.
- Aggressive corporate and national cyberespionage.
- Defensive cartels get to set their pricing.
- Supply chain for attackers as well as defenders grows.
- Organisations and cartels build their own counter-attack teams.
- Within cartels, attack and defensive information is shared, and counter-attack teams collaborate.
Measurables and observables
- Attack patterns: more malware infections and advanced persistent threats.
- Forming of cartels like the Cyber Threat Alliance and Cloud Security Alliance.
- Increased “military speak” in white hat contexts like “Critical Security Controls” and “Certified Ethical Hacker” (EC-Council funded). Security and privacy campaigning NGO’s internally talk about their clients as “target audience”.
- More tools created and gathered in Kali Linux by Offensive Security.
Self-organising (protection) societies
Plot
This is a deviant (partly inductive) scenario, at least in terms of neoliberal official futures.
- Individuals are increasingly targeted by governments and (nation-state or autonomous) hacker groups.
- Individuals are increasingly tracked and profiled.
- Government agencies of various sorts use the information to discover “dissidents”, “criminals” and “terrorists”.
- Businesses and data market companies use the information to influence the emotions and behaviour of individuals.
- Ineffective regulation.
- E-militias form.
- GNU licensed federated social media where users can operate safely within protective boundaries flourish.
A possible response of cartels is that they form their own protection societies for customers. Walled gardens providing anonymity and safety, with steep pricing. A possible response by governments is sicking armies of infiltrators (which may be sophisticated MLM bots) at citizens in the self-organised and corporate run gardens.
Likely effects
- Corporate reputations take a nose-dive, and so does “consumer” trust.
- Bubbles of like-minded people grow (not to be mistaken for filter-bubbles where an algorithm decides what’s in and out of an individual’s bubble). They trade, collaborate and converse between themselves. Trade between groups only happens for mutual beneficial actions or after sufficient trust levels have been established.
- Inequality grows.
- In low-income bubbles, E-commerce drops to an all-time low. So does consumerism to a certain extent. This is also due to extremely low incomes, often way below the poverty line.
- Darknet grows.
- The desire for anonymity grows.
- Differences get slugged out between individuals and between groups.
Measurables and observables
- Appearance of federated GNU licensed self-organising social media, tools like Mastodon, Peertube and research like Tracking Exposed and Citizen Lab.
- Appearance of articles like Freedom Isn’t Free, Wendy Liu
- Corporate run social media user bases like facebook, Twitter, instagram and YouTube expand even further into other regions.
- E-commerce growth rate initially explodes, shops in villages and smaller cities close.
- (Appearance of) Corporate or government run walled gardens.
- In low-income bubbles, E-commerce did not drop to an all-time low. Most likely due to the COVID lockdowns. People in low incomes bubbles do buy less online. The digital divide is clearly there though, even with governments, organisations, and shops pushing their apps.
Raw magic crackled from their spines, earthing itself harmlessly in the copper rails nailed to every shelf for that very purpose. Faint traceries of blue fire crawled across the bookcases and there was a sound, a papery whispering, such as might come from a colony of roosting starlings. In the silence of the night the books talked to one another. A student